How to protect against virus-miners
Technologies / / December 19, 2019

Mikhail Kondrashin
Technical Director Trend Micro in Russia and the CIS.
What are viruses, miners and what they are threatened
In 2017 there was a real boom in Russia cryptocurrency. increased rate Bitcoin and its analogues has drawn attention to the topic of scams and hackers, who began to produce virtual coins dishonest ways: viruses appeared on the Internet-miners that turn infected computers into a network mayningovyh farms. With the world on a string - it turns Mining giant farm with a huge capacity, bringing tens of thousands of dollars monthly.
The scheme of deception is simple and reliable: Hackers launch Internet viruses that spread through email attachments or websites, sources of downloadable content. Virtual "black miners" obsess capacity infected computer hacker pouring virtual coins, and the victim - the electricity bills.
Fortunately, the virus-miners do not spoil the files on your computer and steal data. Their task - to use the computing power of the system for their needs. But still it is bad, especially if the network is infected with the whole enterprise.
How can you pick up a virus-miner
1. Through the launch file
Catch the virus by opening an attachment in a strange letter from an unknown sender. Whether it looks like an image, document, spreadsheet, or file. If you received a letter with a headline like "The salaries of employees" should not be considered as if curious confidential information from falling into your hands. It is enticing (klikbeytnye) headers helps the virus penetrate the computers of naive users.
Trying to download a cracked version of the program fee? It is likely that the hackers have fastened to it the virus-miner.
2. After a visit to the site
Thanks to the development of web technology can become a victim of miners and without infection. For example, CoinHive tool, which is the Java script, makes the miner any device, on which opened a website with an integrated script CoinHive. And mynah not only the computer, but also a smartphone or any other mobile devices with ARM-Internet access.
Most often CoinHive placed on websites where the user spends a lot of time, such as the pirate online cinemas.
3. Through vulnerabilities in the system
Unfortunately, even cautious users can pick up a virus that penetrates through vulnerabilities in the operating system. Everything happens completely unnoticed.
For example, the famous backdoor DoublePulsar, because of which millions of computers around the world were infected with a virus WannaCry, gave birth to a whole family of miners-virus penetrated into the same Windows by.
Developers of operating systems (primarily talking about Microsoft and its Windows) planned to release patches when detecting these vulnerabilities. Therefore, the risk group includes people who fundamentally do not install the update on your computer or do it late.
4. Through the browser extension
Six months ago, the Internet has shaken the history of the expansion of Archive Poster for the Chrome browser, designed for comfortable work with the service Tumblr. As noted by users became popular (more than 100,000 downloads) expansion, Archive Poster developers secretly embedded miner and thus earned their audience.
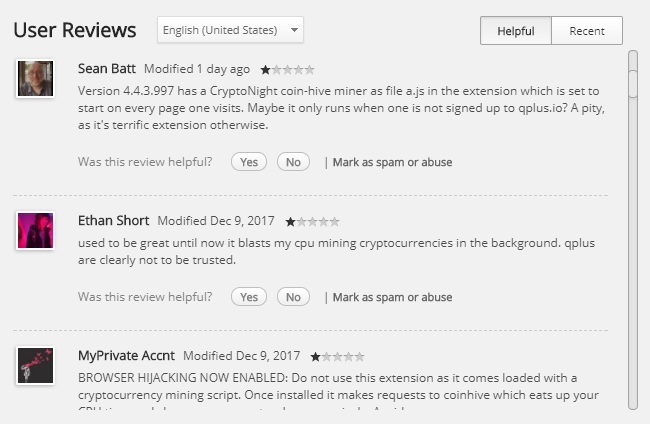
And Google is not in a hurry to clean up harmful expansion of its online store. So before installing the new browser-based extension of at least read the reviews - all of a sudden for the free expansion will have to pay the power of your computer.
Signs of-work miners virus
High system load
Modern computers are very well run and the power does not allow the use of all the processing power in vain. This is especially true of laptops: While browsing, video, or simply their fans are barely audible.
Remember, like the noise of the cooling system is under heavy load like games? If your computer is permanently buzzing and bask system scary brakes and freezes, then its resources someone consumes. And most likely, it is a virus-miner.
Load during periods of inactivity
There are variants of miners, which are included only in the moments of user inactivity. Let's say you leave your computer turned on, but moved away from him. After a few minutes the fans begin to howl, and the miner takes up his dirty work and stops working as soon as you re-takes on the mouse. This way of parasitic existence allows the virus to go undetected for a long time.
Prevention and Treatment
Not all anti-virus software is successfully fighting the miners,. The fact that mining by itself - it is not a process of damage or encrypt files (as in the case of virus-extortionists, for example). If a particular miner is not based antivirus, the virus will be identified as "voracious", but it is a safe application.
If you do not want to become a passive foreign cryptocurrency earner, follow the simple guidelines.
1. Think download
No matter how great the temptation to download pirated apps, music, movies, only legal resources can guarantee security. Together with questionable files on your computer or smartphone probably will get some Trojan.
Expansion of your file should correspond to the type of content that you want to download. Book, music or movie may not have the extension .EXE or .DMG.
If there were suspicions, it is best not to risk it after downloading the file and check it Antivirus. There are many free online scanners such as:
- kaspersky VirusDesk;
- Dr. Web;
- VirusTotal;
- PhishTank;
- Unmask Parasites.
To guarantee better to try once 2-3 resource.
2. Do not open attachments from strange letters
If you received a letter from a stranger with a strange attachment, delete it without a second thought. Most of the investments in the phishing emails are files types .RTF, .XLS and .ZIP, ie text, tables and files, respectively. Executable .EXE files are rare, because they block the sending many e-mail services and integrated IT system protection.
Even harmless Word document or a video can lead to infection miner computer.
The specific name of the malicious file does not exist. They are constantly changing, but always remain attractive names like "moi_foto.zip", "tendery_2018.xls", "zarplaty.doc" and the like.
3. Use a reliable antivirus
known antivirus We learned to catch good miners. Moreover, even if the anti-virus database has not yet added a new modification of the virus-miner, his work can be blocked due to the heuristic analysis. In the description of a number of antivirus software in plain text said about protection against virus-miners. But do not forget that without the daily anti-virus database update becomes useless. Use a hacked copy of antivirus which can not be updated? Assume that the computer was left without protection.
4. update system
Regularly update operating system, antivirus, browser and office applications. The first update is released to fix bugs in applications and close security holes.
For antivirus software it is especially important: in addition to the database, updated filters phishing sites, firewalls, and other important components, which prevents the computer.
Do not forget that you can update the application only through their own interface. If a site suddenly offers to download an update for antivirus, operating system or browser, there you are guaranteed waiting for a virus or trojan. Also, do not install the updates received by mail.

5. Use extension blockers in browsers
Browser extensions, such as No Coin or minerBlock for Chrome and Firefox, MinerBlock for Chrome, will block known viruses-miners working in the browser. Perhaps this is the only way to protect against miners. The main thing - do not prohibit extensions to keep your databases to ensure they remain relevant.
6. There are doubts? Run the "Task Manager"
If you notice that your computer started to slow down, and laptop fans do not stop, you can quickly check the active processes. In Windows, run the "Task Manager" keyboard shortcut Ctrl + Shift + Esc, and on macOS by searching find utility "Monitoring System".
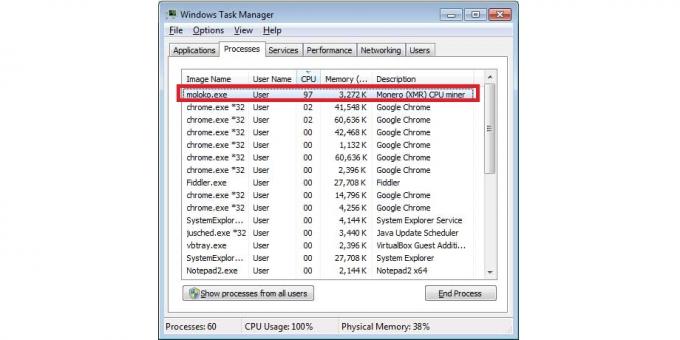
Sort processes by CPU usage and see which one "eats" the most resources. If a process CPU usage by 80-90%, then look for his name on search engines - all of a sudden it is a known miner. At the same time check the Antivirus system.
see also
- Black Mining: How to earn money through other people's computers →
- How to find a web-miner in Chrome →
- 5 reliable firewall to protect your computer →


