Fraud on the Internet: how you can cheat in social networks
Technologies / / December 19, 2019
Fraud in the web takes time, money and nerves. To avoid falling prey to robbers, find out what schemes are found in social networks and how to protect your profile.
"VKontakte», Facebook, «Classmates"
Philanthropic foundations and private collections for treatment
The fees for treatment and care for people is not bad, but it is radically different when we are talking about fraud. Fraudsters use a variety of schemes to raise money, and the end result is the same: the money comes at the expense of a third party rather than to the treatment or care.
Before you send money to a fund or a private person, check out:
- Detailed reports on income and expenditure.
- For information on how to withdraw that money, as well as the final figure fees.
- Information about a person or a fund that collects money.
If you are not sure or can not find the necessary information, ask questions directly to the fund. Honest organization will tell you about themselves and their work. Fraudsters often create an emotional noise, without providing details. Lists of funds that can be trusted, is on the site "
gift a life"And"Together».Account hacking
Almost all of us get messages asking for help in a difficult situation. Scam different is that they are asking for help exclusively in cash. In such cases, the attackers are trusted relatives and friends of a person coming up with a variety of stories.
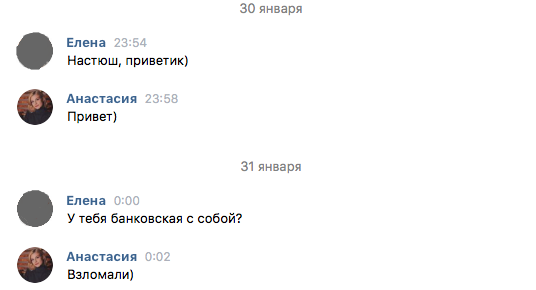
If this is your close friend, call him on the cell phone and ask about what happened. If you communicate rarely ask for facts and a phone number where you can be contacted.
Do not transfer money to a person not yet talk with him personally.
To protect your account from hacking, check your password. Secure password consists of 9 characters or more, containing uppercase letters, numbers and symbols. The same rules apply to the address to which to register an account.
Phishing apps and sites
Phishing - kind of Internet fraud in which user data leaked through false applications and websites.
Phishing attackers to create a copy of a popular website or application, and actively disseminate it. Excuses to go to the link may be very different from the notification of the hosts to threats drain intimate photos. In any case, do not open links and attachments from strangers.
Before proceeding, check the link address is correct. Fraudsters often use in their work errors. For example, the address vkontakte.w6.ru It does not apply to the social network "VKontakte" and can be used for phishing.
Modern browsers have anti-phishing protection and warn you about unsafe sites. By the way, be careful - phishing and distributed via SMS.
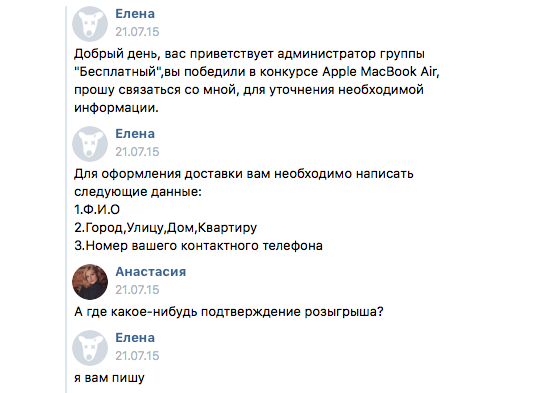
Win prizes or sudden inheritance
You will be asked to pay for the delivery of a gift or a job lawyer who will prepare a paper on the inheritance. Driving with gifts is often applied to users who participate in the sweepstakes by repost. Fraudsters can play anything from a free manicure to a car and an apartment in Moscow.
To see through the fraudster, ask enough evidence that what you have won, and not someone else.
Groups "give free"
In groups "give free" offer to exchange participants or just to give unnecessary things. To get a free thing, a community member makes a repost of interest entry. After a certain time the donor chooses a person from the list to share and agree on the transaction.
Children's toys, tables and dishes do not arouse suspicion, but often you can stumble upon announcement of expensive household appliances and digital devices. Deception can distinguish the following criteria:
1. Closed comments and the lack of a signature in the ads. In these groups, participants interact and ask questions about your product. In groups of swindlers comments are closed.
2. You are asked to pay shipping. "The thing is already yours, you just need to pay shipping", - assured unscrupulous donors. In real life, people do not engage in unnecessary delivery of them things.
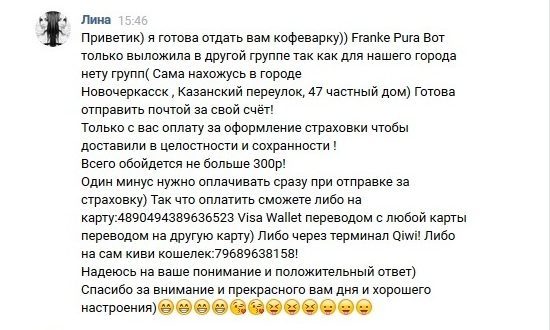
3. Transfer of things does not happen directly. The administration of these groups in the transaction is not involved, but in groups of scams transactions take place through the guarantor. Guarantee - the mediator between the recipient and the donor. He warns you of fraud, and then asked to pay for their services and delivery of goods. Later guarantor informs you that the seller turned out to be dishonest, and returns you to the shipping cost, but the cost of the services it does not compensate.
4. Scammers use photos from the Internet. In any case, check finding images.
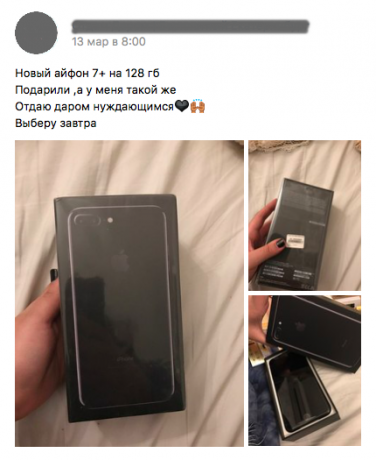
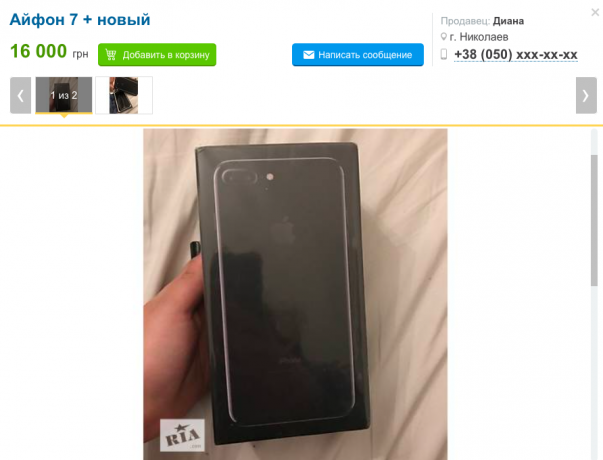
Instagram is very different from other social networks, so the fraud scheme in it others.
One of the most recent - the creation of fake web accounts with promises of free branded items or discounts. You do repost, you fill out the form, mail notifications of winning and the number of purse, through which you can pay the shipping. When the profile of collect enough money, the attackers is removed.
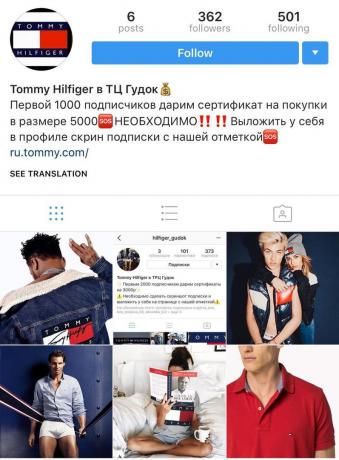
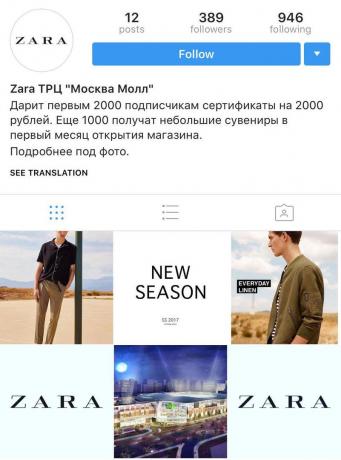
If you doubt the authenticity of the profile, write directly to representatives of the official store. They are prompt, whether it is a real event or a regular divorce.
Another scheme - accounts for cheating likes and subscribers. These profiles offer to make your page popular for a small fee, and after the transfer of the required amount lost. There is only one piece of advice - do not get fooled.
Researchers at the University of Southern California have establishedOnline Human-Bot Interactions: Detection, Estimation, and Characterization. That the proportion of bots on Twitter is 9-15%. It is about 48 million users.
Fraud schemes in Twitter are similar to all other social networks, but there is a difference. The size of a tweet is 140 characters, so widespread reduction services for links among users. And scammers take advantage of this. Short link does not show the source address of the page, so it is impossible to understand in advance, the user navigates to a site.
For short link can be hidden and malicious phishing sites.
Therefore, it is not necessary to click a link, if you have doubts about the profile, which distributes it.