How to protect personal data on the Internet
Technologies / / December 19, 2019
Attackers every day steal personal information of celebrities and ordinary users. Recently accounts hacked US presidential candidate Hillary Clinton, Deputy Energy Minister of Russia Anton Inyutsyna, journalist Dmitry Kiselyov.
Many people think that their data criminals are not interested, but experience shows that fame does not affect the desire of criminals to catch other people's personal information, and benefit from them. We have reviewed the most popular scenarios in which your data is at risk, and tell you what to do to keep your personal information confidential.
Where danger awaits?

E-mail is more than just a mailbox. You use it to register on most sites and services, and thus gain access to the mail, the attackers will be able to hack into your other accounts.
It has not been canceled and the threat of secret correspondence stored in the Document. If it is a working box, the confidential corporate information could get to hackers. And then hacked email is not just your problem - would threaten the safety of all correspondence with the company.
Accounts in the game services
Millions of people play World of Tanks, DOTA 2, Counter Strike: Global Offensive, or FIFA, use Origin, Steam, Xbox Live, PlayStation Network and other online gaming services.
Members earn game experience, game currency, buy things for real money for game equipment, games themselves. Hack your game account, attackers steal purchased licensed games, game equipment and items - and get real money for them.
Social networks and instant messenger
Social networks and instant messenger - the best facilities for scammers if they want to profit intimate details of your life. We all have skeletons in the closet, but it does not mean that they should be made public. If you do not properly protect your account, the trouble can happen anytime.
For many correspondence in social networks and messengers replaces the email - they share photos, documents, other confidential information.
Digital theft of a smartphone
All modern smartphones have a basic account: for iOS is Apple ID, for Android - Google Account. If intruders get access to them, valuable information about you and your smartphone will be in their hands.
In the last year it has become known story about the scams that fraudulently gained access to the Apple ID, blocked the victim's phone and demanded money for unlocking. This often happens when buying smartphones, when an unscrupulous seller sells you, in fact, the brick, which can not be used without entering the password to the compromised account.
Mobile Apps and Games
Programs installed from the App Store, Google Play or Windows Marketplace, request access to the data: your contacts, geopozitsii, calendar, payment data. Every time read carefully what information requests to access the app or game. For example, what puzzle game know your location and what converter need your calendar?
Bank data

Who is paying bank cards not only in the usual supermarket: pay card utility bills through online banking and shopping in online stores, with the help of the map book the air tickets and hotels. But think about where you leave your details?
Insecure Wi-Fi-point
Wi-Fi - happiness for the traveler and freelance. But attackers are insecurity of open points, and the unwary user. By the way, the hackers are selected and password-protected points. And already there is a trick: Connect to Wi-Fi, and all that you are doing on the screen and enter on the keyboard, the attacker sees.
It is important to understand what information and who you trust. There is no problem to entrust their email to Google. But if access to the same e-mail requests unfamiliar application, give such access is dangerous not only because of the lack of information on the good reputation of the service. Attackers can break into the application itself, and thereby gain access to the information even without the need to hack your Google-account.
How to protect your data?

As you can see, the problem of security on the Internet is becoming more relevant than ever. Everywhere there is a risk of getting caught on a fishing tackle cybercrime. We will talk about the basic ways of protection of personal data, which should definitely be practiced.
Two-factor authentication
Sounds not clear, but in reality everything is simple: it is a double protection, the first line of which - the usual combination of user name and password, that is what is stored on the server, and the second - something that has access to only a specific user. We talked about five ways two-factor authentication, including SMS-passwords, application authenticators and hardware tokens.
A simple example: you enter the login and password from online banking after the phone comes a special SMS-code. This is the two-factor authentication.
Two-factor authentication is supported by Google, Apple, Microsoft, Facebook, «VKontakte" Dropbox, Telegram and others. This is a necessary measure to protect the data, so be sure to include a two-stage protection in all accounts. If some kind of service does not support it, this is a serious reason to stop using it.
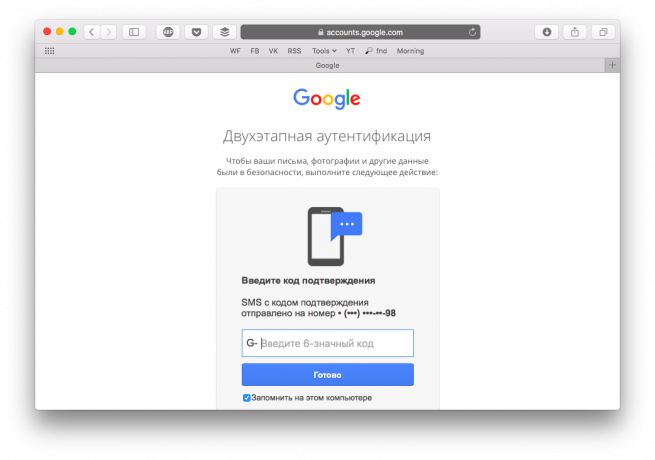
For what is suitable: E-mail accounts in social networks and instant messengers, games accounts for smart phone account, Internet bank.
secure connection
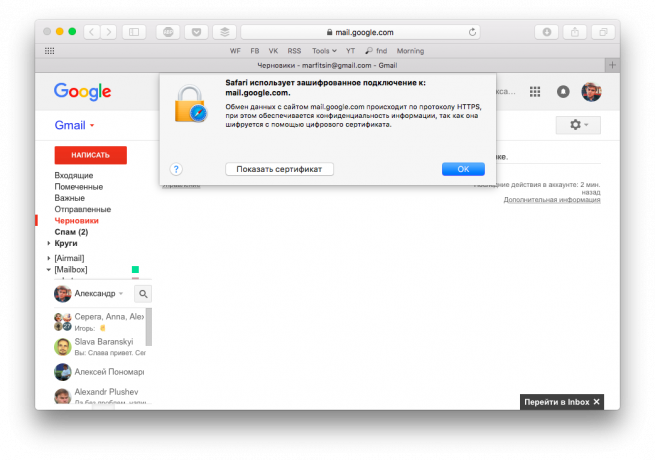
Back in 2008, we wrote that the postal services should be used only with a secure connection. After 8 years, this advice only became more urgent. The benefit of the majority of social networks to learn to work with the HTTPS-protocol, it also moved online banking and payment services.
Making purchases and other potentially dangerous actions, look at the icon to the left of the address bar. Make sure that you are working with a site over an encrypted connection.
If you can not work with a secure connection, you can use special services, such as Disconnect.me. It redirects the user to a HTTPS-version of the site.
Another application that automatically redirects you to the HTTPS-version, - HTTPS Everywhere. There are extensions for most popular browsers.
Price: 0

Developer: developer
Price: Free

Price: Free
For what is suitable: E-mail accounts in social networks and instant messengers, games accounts for smart phone account, Internet bank.
password Managers
"Come up with a complex password" - this is the advice in each article for the protection of personal data. But it is unlikely you will come up with a password more complex than a password generated by the special services, and even come up, where you will store it: in the head on a piece of paper?
You can also change your password often, you might say. But just a few weeks ago, experts UK Government Communications Headquarters explained why frequent change the password only hurts data security.
There are special password managers that take the headache itself. They generate complex passwords, store them in a secure vault and you do not need to remember the password to a particular site - the application will substitute itself in his desired field. The most popular services: 1Password, LastPass, Enpass.
For what is suitable: E-mail accounts in social networks and instant messengers, games accounts for smart phone account, Internet bank.
Monitors access to your data
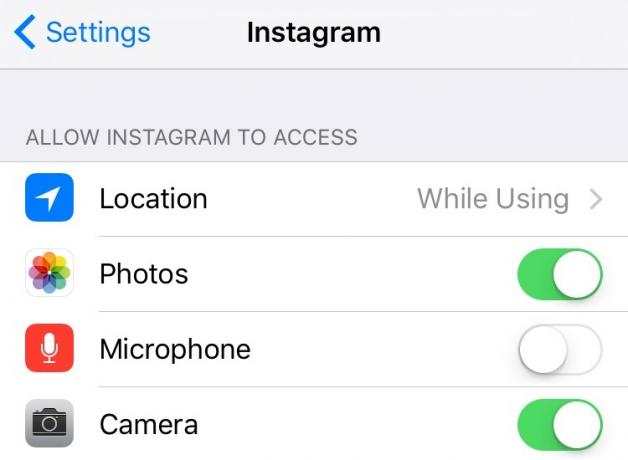
iOS users, and more recently, AndroidCan manage apps accessing various data. Take the time and spend the audit: check what information has access to the installed applications and games. If any of the access requests are suspicious - turn off.
For what is suitable: mobile applications.
Use a VPN, working with public Wi-Fi-points
Working in cafes and other public places with Wi-Fi, VPN-use service. He will redirect traffic to their own server, and you give up already "cleaned", which can not keep track of criminals. Remember that the password access does not guarantee safety.
We talked about best free VPN-services for Google Chrome browser. VPN recently, the company has built into its browser Opera. Do not miss out and a detailed guide the most popular VPN-servicesWhich was That One Privacy Guy site.
For what is suitable: Open Wi-Fi-point.
conclusion
As you can see, your personal data at risk every day. Briefly summarize our recommendations for the protection of personal information on the web.
- Turn on two-factor authentication on all sites and services.
- Work with a secure connection, or use the program to encrypt the traffic.
- Use a password manager. Do not change your password often.
- Watch as the mobile app uses personal data.
- Use a VPN, with an open Wi-Fi-points.


