Ghosts on the net. 10 most high-profile cyberattacks in history
Miscellaneous / / August 04, 2021
From hacking stars' accounts to attacking Iran's nuclear program.
10. DarkHotel. The tarnished reputation of luxury hotels, 2007-2014
The malicious spyware, also known as Tapaoux, was distributed by attackers"Dark Hotel": a cyber espionage network in Asian hotels / Kaspersky Daily through open Wi-Fi networks in a number of premium hotels. Such networks are very poorly protected, which is why hackers easily managed to install their software on hotel servers.
In the Telegram channel “Life hacker»Only the best writing about technology, relationships, sports, cinema and more. Subscribe!
In our Pinterest only the best texts about relationships, sports, cinema, health and much more. Subscribe!
On computers connected to Wi-Fi, it was proposed to install an official update of some program at first glance. For example, Adobe Flash or Google Toolbar. This is how the virus was usually disguised.
The hackers also used an individual approach: once DarkHotel pretended to be a torrent file to download a Japanese erotic comic book.
After getting on the device, the virus program offered to enter personal data, for example, the card number, when "updating", and also knew how to read keystrokes when typing. As a result, the attackers gained access to the usernames and passwords, as well as his accounts.
Hackers deliberately set up a virus in a hotel chain before the arrival of high-ranking guests in order to gain access to their devices. At the same time, the attackers knew exactly where the victim would live, and they configured the program so that it would infect only the device they needed. After the operation, all data from the servers was deleted.
DarkHotel's targets were top managers of large companies, successful entrepreneurs, high-ranking politicians and officials. Most of the break-ins were done'Dark Hotel' Hacks Target Business Travelers: Report / NBC News in Japan, China, Russia and Korea. Having received confidential information, hackers, apparently, blackmailed their victims, threatening to spread classified data. The stolen information was also used to search for new targets and organize the next attacks.
It is still unknown who was behind these cybercrimes.
9. Mirai. The Rise of Smart Devices 2016
Together with the boom of various devicesconnected to the Internet - routers, smart homes, online cash registers, video surveillance systems or game consoles - there are also new opportunities for cybercriminals. Such devices are usually poorly protected, so they can easily be infected by a botnet. With its help, hackers createWhat is a cyberattack? / Cisco networks of compromised computers and other devices, which are then controlled without the knowledge of their owners.
As a result, devices infected by botnets can spread the virus and attack targets defined by hackers. For example, to overwhelm the server with requests so that it will no longer be able to process requests and communication with it will be lost. This is called a DDoS attack.
The botnet with the sonorous name Mirai ("future" from Japanese) has become especially famous. Over the years, it infected hundreds of thousands of network-connected routers, surveillance cameras, set-top boxes and other equipment whose users did not bother to change their factory passwords.
The virus entered devices through a simple selection of a key.
And in October 2016, this whole armada receivedK. Kochetkova. What happened to Twitter, PayPal, Amazon and other American services / Kaspersky Daily signal to fill up with calls from the provider domain names Dyn. This drove PayPal, Twitter, Netflix, Spotify, PlayStation online services, SoundCloud, The New York Times, CNN, and about 80 other Dyn user companies down.
The hacker groups New World Hackers and RedCult claimed responsibility for the attack. They did not put forward any requirements, but the total damage from downtime of online services was about $ 110 million.
It was possible to fight off Mirai by redistributing traffic and restarting individual components of the Dyn system. However, what happened raises questions about the security of smart devices, which can account for almost half the capacity of all botnets.
8. Scandalous leaks of personal data of celebrities from iCloud and Twitter, 2014 and 2020
Plums caused a real resonance.
iCloud
Cybercriminals can get hold of users' personal data by sending fraudulent messages. For example, SMS masquerading as warnings from the security service. The user is told that they are allegedly trying to get into his profile. Fake tech support offers to follow a link that actually leads to the attackers' site and fill out a questionnaire with a username and password in order to protect personal data. Having seized the information of a gullible person, scammers gain access to the account.
In 2014, in this way, hackers managed toC. Arthur. Naked celebrity hack: security experts focus on iCloud backup theory / The Guardian hack iCloud of a number of celebrities and make their personal data freely available. The drain was not so much extensive as loud. For example, personal photographs of celebrities have gotten to the Internet, including very spicy pictures. In total, about 500 images were stolen. Moreover, it is possible that not all of them were published.
Kim Kardashian, Avril Lavigne, Kate Upton, Amber Heard, Jennifer Lawrence, Kirsten Dunst, Rihanna, Scarlett Johansson, Winona Ryder and others suffered from the hack.
Within four years after hacking five were found and arrestedFormer Hanover teacher sentenced in ‘Celebgate’ nude photo hacking / WTVR hackers from the United States involved in it. Four received between eight and 34 months in prison, and one managed to get off with a $ 5,700 fine.
In July 2020, they got under the distributionTwitter Hack / Twitter Support Thread famous Twitter users. One of the burglars convinced social network employee who works in the IT department. This is how the hackers gained access to the accounts they needed. And then they posted posts there with a call to support Bitcoin and send money to the specified crypto wallet. From there, the funds were supposedly to be returned in double the amount.
Various famous personalities again became victims: Bill Gates, Elon Musk, Jeff Bezos, Barack Obama and other American celebrities.
Also, some corporate accounts - for example, Apple and Uber. In total, about 50 profiles were affected.
Social networks had to temporarily block hacked accounts and delete fraudulent posts. However, the attackers managed to raise a good jackpot on this scam. In just a few hours, about 300 users sent more thanE. Birnbaum, I. Lapowsky, T. Krazit. Hackers took over Twitter after ’a coordinated social engineering attack’ on employees / protocol 110 thousand dollars.
Burglars turned out to beStatement from FBI San Francisco Assistant Special Agent in Charge Sanjay Virmani on Arrests in Twitter Cyber Attack / FBI San Francisco three guys and one girl between the ages of 17 and 22 from the USA and the UK. The youngest of them, Graham Clark, managed to disguise himself as a Twitter employee. Now young people are awaiting trial.
7. GhostNet. China vs. Google, Human Rights Defenders and the Dalai Lama, 2007-2009
Cyber attacks and cyber espionage are carried out not only by hacker groups, but also by entire states. Thus, Google felt the full power of the hackers in China's service.
In 2009, the company discovered that it had been distributing spyware using its server in China for two years. She infiltratedJ. Markoff. Vast Spy System Loots Computers in 103 Countries / The New York Times at least 1,295 computers in government and private companies in 103 countries.
Resources were affected, ranging from foreign ministries and NATO to the Dalai Lama's shelters. Also, the GhostNet has damaged more than 200 US firms.
With the help of the virus, China monitored the governments of South and Southeast Asia, as well as Chinese dissidents and human rights activists. The program, for example, could activate the cameras and microphones of the computer in order to eavesdrop on what was being said nearby. Also, with its help, Chinese hackers stole the source code of the servers of individual companies. Most likely, he was needed to create their own similar resources.
The discovery of GhostNet played a big role in the fact that Google closed its business in China, not holding out in the Middle Kingdom for five years.
6. Stuxnet. Israel and the United States vs. Iran, 2009-2010
Typically, cyberattacks require the victim to be connected to the Internet. However, in order to spread malware even among those computers that do not have access to the Internet, attackers can infect USB flash drives.
This technique was very effectively used by the special services of the United States and Israel, who wanted to slow down the Iranian program to create nuclear weapons. However, the country's nuclear industry facilities were isolated from the World Wide Web, which required an original approach.
The preparation for the operation was unprecedented. The hackers developed a sophisticated complex virus called Stuxnet that acted with a specific purpose. It only attacked Siemens industrial software. After that, the virus was testedW. J. Broad, J. Markoff, D. E. Sanger. Israeli Test on Worm Called Crucial in Iran Nuclear Delay / The New York Times on a similar technique in the Israeli closed city of Dimona.

The first five victims (Iranian companies working in the nuclear industry) wereStuxnet: start / Kaspersky Daily carefully selected. Through their servers, the Americans managed to distribute Stuxnet, which unsuspecting nuclear scientists themselves brought onto secret equipment via flash drives.
The break-in led to the fact that the centrifuges, with the help of which the Iranian nuclear scientists enriched uranium, began to rotate too fast and fail. At the same time, the malicious program was able to simulate normal operation readings so that specialists would not notice failures. Thus, about a thousand installations were put out of action - a fifth of such devices in the country, and the development of Iran's nuclear program was slowed down and thrown back for several years. Therefore, the story with Stuxnet is considered the largest and most successful cyber sabotage.
The virus not only fulfilled the task for which it was created, but also spread among hundreds of thousands of computers, although it did not cause much harm to them. The real origin of Stuxnet was only established two years later after 2,000 infected files were examined.
5. BlueLeaks. Biggest U.S. security agency data theft, 2020

American intelligence agencies themselves were vulnerable to hacker cyberattacks. Moreover, the criminals have demonstrated that they can also use cunning schemes. For example, attackers did not enter government systems, but hacked a web development company Netsential, which provided federal and local agencies with technical sharing capabilities information.
As a result, hackers from the Anonymous group managed toA. Greenberg. Hack Brief: Anonymous Stole and Leaked a Megatrove of Police Documents / WIRED steal more than a million files of American law enforcement and intelligence services: only 269 gigabytes of information. The attackers published this data on the DDoSecrets website. Video and audio clips, emails, memos, financial statements, as well as plans and intelligence documents were made publicly available.
Although there was no classified information or data on the violation of the law by the law enforcement officers themselves, much of the information was rather scandalous. For example, it became known that the special services were monitoring activists Black Lives Matter. Enthusiasts began to parse the merged files and then publish them under the hashtag #blueleaks.
Despite preliminary checks performed by DDoSecrets, confidential data were also found among the leaked files. For example, information about suspects, victims of crimes and bank account numbers.
At the request of the United States, the DDoSecrets server with BlueLeaks data in Germany was blocked. A criminal case has been opened against Anonymous, but there are no specific suspects or accused yet.
4. Attack on the servers of the Democratic Party of the United States, 2016
Due to the confrontation between Hillary Clinton and Donald Trump, the 2016 US presidential election was scandalous from the very beginning. They culminated in a cyberattack on the resources of the Democratic Party, one of the country's two main political forces.
The hackers were able to install a program on the Democrats' servers with which they could manage information and spy on users. After abductions the attackers hid all traces behind them.
The information received, which is 30 thousand emails, was handed over to WikiLeaks by hackersHillary Clinton Email / WikiLeaks. Seven and a half thousand letters from Hillary Clinton became the key ones in the leak. They found not only personal data of party members and information about sponsors, but also secret documents. It turned out that Clinton, a presidential candidate and senior politician with experience, sent and received confidential information through a personal mailbox.
As a result, Clinton was discredited and lost the election to Trump.
It is still not known for certain who was behind the attack, but American politicians persistently accuse Russian hackers from the Cozy Bear and Fancy Bear groups of this. They, according to the American establishment, have previously participated in hacking the resources of foreign politicians.
3. Hacking NASA and the US Department of Defense by a 15-year-old teenager, 1999
Jonathan James, a teenager from Miami, had a passion for space and knew the Unix operating system and the C programming language like the back of his hand. For fun, the boy looked for vulnerabilities in the resources of the US Department of Defense and foundK. Poulsen. Former Teen Hacker's Suicide Linked to TJX Probe / WIRED them.
The teenager managed to install a spyware program on the server of one of the divisions to intercept official correspondence. This gave free access to passwords and personal data of employees of various departments.
Jonathan also managed to steal the code used by NASA to maintain the life support system on ISS. Because of this, the work on the project was delayed by three weeks. The cost of the stolen software was estimated at $ 1.7 million.
In 2000, the boy was caught and sentenced to six months of house arrest. Nine years later, Jonathan James was suspected of participating in a hacker attack on TJX, DSW and OfficeMax. After interrogation, he shot himself, saying in a suicide note that he was innocent, but did not believe in justice.
2. WannaCry. Data Encryption Epidemic 2017
One of the most unpleasant types of malware is data ransomware. They infect your computer and encode files on it, changing their type and making them unreadable. After that, such viruses display a banner on the desktop with a request to pay redemption for unlocking the device, usually in cryptocurrency.
In 2017, the Internet was swept by a real epidemic of wcry-files. This is where the name of the ransomware comes from - WannaCry. To infect, the virus used a Windows vulnerability on devices with an operating system that had not yet been updated. Then the infected devices themselves became breeding grounds for the virus and spread it on the Web.
First discovered in Spain, WannaCry infected in four daysA. Hern. WannaCry, Petya, NotPetya: how ransomware hit the big time in 2017 / The Guardian 200 thousand computers in 150 countries. The program also attacked ATMs, vending machines for tickets, drinks and food, or information boards running on Windows and connected to the Internet. The virus also damaged equipment in some hospitals and factories.
It is believed that the creators of WannaCry were originally going to infect all Windows devices in the world, but did not manage to finish writing the code, accidentally releasing a virus on the Internet.
After infection, the creators of the malicious program demanded $ 300 from the owner of the device, and later, when the appetite was playing up, $ 600 each. Users were also intimidated by "setting on the counter": supposedly in three days the amount would increase, and after seven - the files would be impossible to decrypt. In fact, in any case, it was impossible to return the data to its original state.
Defeated WannaCry researcher Markus Hutchins. He noticed that before infection, the program was sending a request to a non-existent domain. After its registration, the spread of the virus stopped. Apparently, this is how the creators intended to stop the ransomware if it got out of control.
The attack turned out to be one of the largest in history. According to some reports, she causedRansomware WannaCry: All You Need to Know / Kaspersky $ 4 billion in damage. The creation of WannaCry is associated with the hacker group Lazarus Group. But no specific culprit has been identified.
1. NotPetya / ExPetr. The biggest damage from the actions of hackers, 2016-2017
A relative of WannaCry is another ransomware known under suspiciously Russian names: Petya, Petya. A, Petya. D, Trojan. Ransom. Petya, PetrWrap, NotPetya, ExPetr. It also spread over the Web and encrypted the data of Windows users, and paying a ransom of $ 300 in cryptocurrency did not save the files in any way.
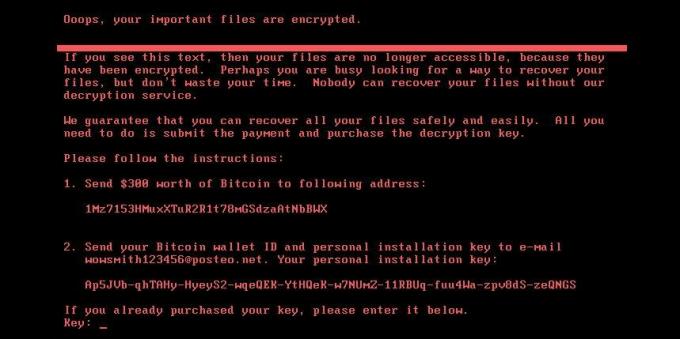
Petya, unlike WannaCry, was specifically targeted at businesses, so the consequences of the attack turned out to be much greater, although there were fewer infected devices. The attackers managed to seize control of the MeDoc financial software server. From there, they started spreading the virus under the guise of an update. The mass infection appears to have originated from Ukraine, which the malware caused the most damage.
As a result, a wide variety of companies around the world were affected by the virus. For example, in Australia there wasPetya cyber-attack: Cadbury factory hit as ransomware spreads to Australian businesses / The Guardian production of chocolate, in Ukraine came outBUT. Linnik. What have you done, Petya / Gazeta.ru cash registers were out of order, and in RussiaTour operator "Anex" stopped sales due to cyber attack / Fontanka.ru the work of the tour operator. Some large companies also suffered losses, such as Rosneft, Maersk and Mondelez. The attack could have had more dangerous consequences. So, ExPetr hitDue to cyber attacks, monitoring of the Chernobyl nuclear power plant was transferred to manual mode / RIA Novosti even on the infrastructure for monitoring the situation in Chernobyl.
The total damage from hacking amounted toWhat can we learn from the "most devastating" cyberattack in history? / CBC News more than $ 10 billion. More than any other cyber attack. The US authorities have accusedSix Russian GRU Officers Charged in Connection with Worldwide Deployment of Destructive Malware and Other Disruptive Actions in Cyberspace / The United States Department of Justice in the creation of "Petit" the Sandworm group, which is also known as Telebots, Voodoo Bear, Iron Viking and BlackEnergy. According to American lawyers, it consists of Russian intelligence officers.
Read also👨💻🔓🤑
- Black mining: how to make money through other people's computers
- 14 incredibly cool films about programmers and hackers
- How security professionals protect personal information
- Online scam: how you can be scammed on social media
Scientists talk about dozens of COVID-19 symptoms that can persist for more than 6 months
Scientists have named the characteristic symptoms of the delta strain of coronavirus. They are different from the usual COVID-19

