11 signs of hacking your computer or smartphone
Technologies / / December 19, 2019
1. Unexplained debiting
The first thing that might make you think about a possible burglary - is the sudden withdrawal of funds to which you have no relationship. This is a clear sign that the fraudsters can get access to information about your card or "hijacked" an account of one of the payment services used by you.
If your funds balance is always at hand, you will notice suspicious activity quickly. If you rarely check the score and you do not even connected notification via SMS or e-mail, it's time to do it.
Messages with the codes to confirm the purchases, which you, of course, did not commit, ignore, too, is by no means impossible. Regardless of whether the sender is known to you or not, you should immediately block the card and go to the bank.
2. Slowing device operation
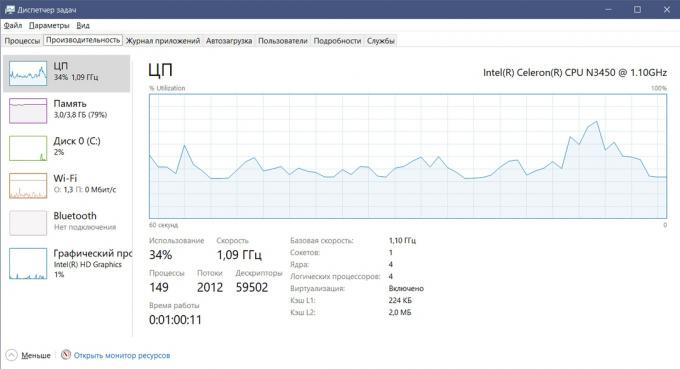
Work to sneak into your computer or smartphone malware may require high computing power. Therefore, if you notice a decrease in performance, which is a significant, unexpected and long-term - should immediately check the device for viruses and limit this period any network activity. If a threat was found, possibly slowing down the reason
lies elsewhere.3. Disabling or interruptions in the work of security software
If malware crept in and has had time to grow roots, it is possible that it will try to shut down or isolate all hazardous remedies for it. Reason to sound the alarm - disabling involuntary antivirus or the inability to launch a computer scan on demand. Avoid such a situation will allow constant updating of antivirus databases and downloading applications only from trusted sources.
4. Changing software or browser settings without your participation
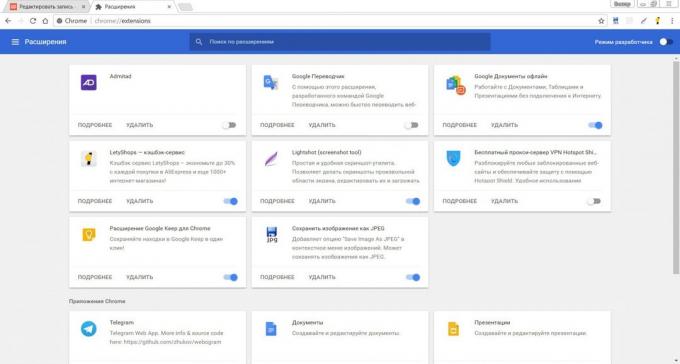
If protection of your device missed at least one malicious program, then soon they can become much larger. Entrenched on the PC threats can initiate downloading additional malicious tools that can be presented as additional software and browser-based extensions.
Check what software is active at the time of your computer, you can use the "Task Manager" on Windows (cause the key combination Ctrl + Alt + Del) and "Monitoring System" on MacOS (see the list of "Utilities" or "Program"). You need to open a list of all the extensions and in a similar way to check in your browser that is installed and it will start automatically.
5. Increasing the number of pop-ups
Through a browser, and some other malware applications can bombard you with pop-ups on the need to carry out a computer scan or test the login credentials. These windows often look quite authentic and not arouse suspicion, but if they began to appear more frequently than ever before, it is an occasion to reflect.
Now modern browsers and operating systems generally do an excellent job with annoying vsplyvashkami, but the likelihood that the initiator of the show the next window or banner is to get to the PC malware, yet there is.
6. Changes in the system settings
Malicious applications may completely change, and system settings. A classic example - this change your browser's homepage or search engine. Seeing a completely new and still quite dubious page when loading the same Chrome or Firefox, we follow links on it, of course, it is not necessary.
Especially closely watch for requests to change system settings, and the issuance of permits for new programs. The latter is very important in the case of smartphones, where, apparently, the elementary applications may require a list of rights of access in the bowels of the gadget.
7. Uncontrolled device Activity
If you sometimes feel that your computer or smart phone lives its own life, it is likely that they are someone manages remotely. This is done through the backdoor application that you can download together with the newly downloaded content.
This remote access can be tracked on the involuntary exit device from sleep mode, hard disk activity in a sudden moment of idle PCs and even in spontaneous mouse cursor movement. Fortunately, in recent years so brazen hacks are extremely rare, especially if you are using only licensed software.
8. Sudden shutdown and restart
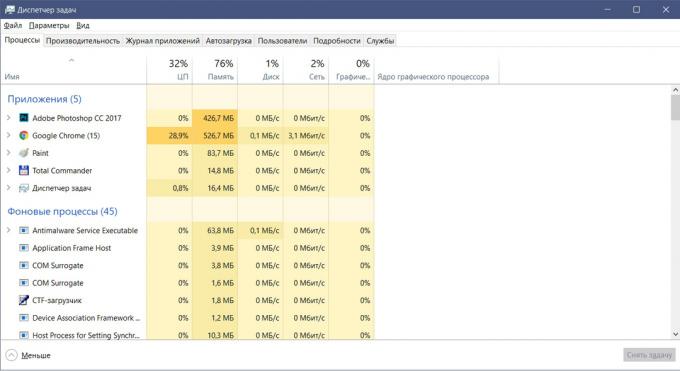
In addition to activity in the system, the malware may cause a sudden shutdown or reboot the device. This may well speak of partial control over PC and attempts to destabilize the system.
Panic here costs only when such frequent disconnection and prerequisites for that was not: you do not overload the PCs demanding games and control heating. In these cases, again, it's worth checking the active processes in the "Task Manager" and in particular the autorun.
9. Sending messages without your knowledge
In the case of access to your mail attackers try to spread its tentacles as far as possible. Spamming on your behalf - the first thing you should pay attention. Daily check not only new mail, but also sent messages folder. Noticing something suspicious, hurry to change password on this account, and to do so better through another device.
10. Suspicious online activity
You can become a source of spam not only in email, but also in social networks. And usually the one sending messages attackers are not limited. If it is, for example, Twitter, hacked account could say a lot of new subscriptions and comments under false posts. And the trouble is that all this can be found only after some time that your account has already been used to the maximum.
To protect yourself from this is possible only by means of vigilance, that is, periodic verification of the main activities in each network. In case of detection of suspicious messages and comments that you could not even leave drunk, sure to change your password using this for other devices.
11. Denial of access to your accounts
If the authorization in any of the services your default password suddenly came up, it is likely that an attacker who gains access to your account, managed to change it. In case it is not necessary to panic with a major service or social network. You can help restore the shape and change the password through the mail or direct appeal to tech support.
To increase the level of protection for all your accounts and social networks, it is necessary to use two-factor authentication.
Total
Even if you think that the danger had passed and data accounts were not affected, to be safe, definitely worth it. Once again, recall that always makes sense to periodically update the passwords of their accounts, especially if the same password is used in multiple services.
If any of the online account yet been compromised, report it immediately to support. Even if you can easily regain access to do so still worth it, because you do not know where the "stolen" account had time to use.
On the PC, be sure to install a reliable antivirus databases with fresh or at least systematically check the system with light portable-options. If for some reason on the infected computer to install or run such software fails, you need to download the program through another device and then try to copy.
It is possible that for a full recovery may need to reset the system. In this case, you need to take care of backup important data for you. The benefit of it is now possible to do on any device, regardless of operating system.



