Guide for the paranoid: how to avoid surveillance and data theft
Technologies / / December 19, 2019
Windows is spying on you, sending telemetry to Microsoft, and Google stores your searches and analyzes the contents of the letters to fill up your advertising. Of course, you can simply do not pay attention to it. But not only large corporations interested in your data. It can be simple swindlers and extortionists. Even your relatives, or colleagues, opening your laptop can see something that is not intended for prying eyes.
To protect your files, passwords, correspondence and other confidential information, you need to take care of security. Necessary to perform absolutely all the requirements set out below. But you can review them and decide which of these can be useful for you.
encrypt data
Even if your system is protected by a password, the attacker can easily reset it by booting from an external drive if you leave your computer unattended. Reset your password and do not need - any Live-Linux distribution can easily read and copy your data. Therefore it is necessary to take measures for the encryption.
And Windows, and MacOS, and Linux have built-in encryption. Take advantage of them, and your documents will be inaccessible to outsiders, even if your laptop falls into the wrong hands.
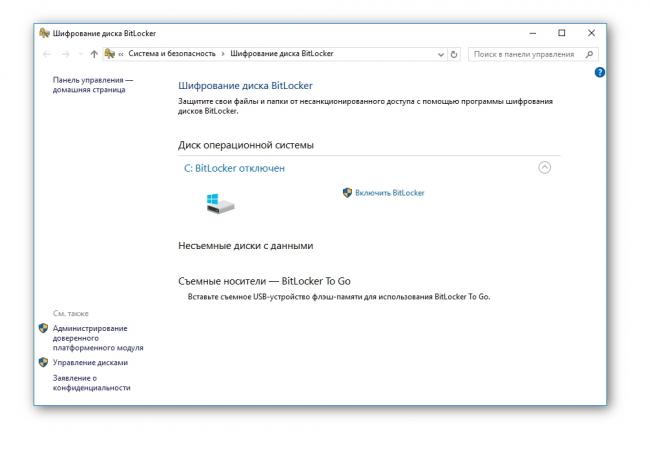
Windows has a built-in BitLocker encryption tool. Open the "Control Panel", go to the "System and Security" and select "Disk Encryption BitLocker».
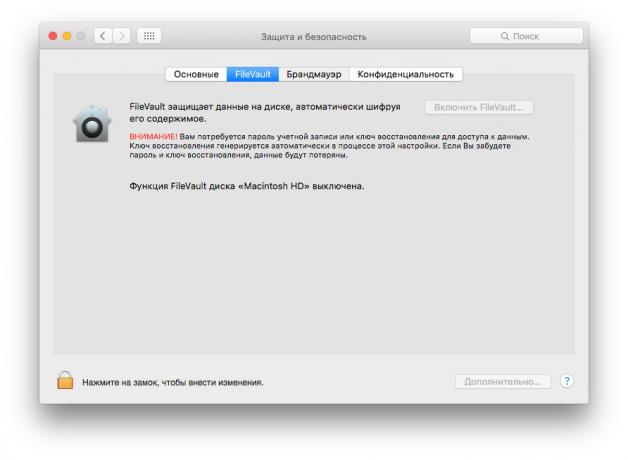
In macOS data encryption can be effected using FileVault. Go to "System Preferences", find the section "Safety and Security" and open the FileVault tab.
Most Linux distributions tend to offer encrypt your home partition when installing the system. When you format a section that creates an encrypted file system eCryptfs. If you have neglected it during system installation, later you can encrypt the desired sections manually using the Loop-AES or dm-crypt. To learn how to do this, check out instructions.
More advanced encryption function can be used free cross-platform tool open source VeraCrypt. In addition to simple encryption, it can create fraudulent sections with unimportant information that may distract attention from burglars really valuable data.
Upload VeraCrypt →
Be careful with encryption. If you forget your password, restore the data will not work. In addition, ensure that your computer is protected from accidental voltage drops. If during operation the encrypted disk device suddenly shut down, data can be lost. And do not forget on backups.
Use a password manager
Used as a password meaningful phrases and remember them - this is not the best idea. Use a password manager. Generated each time a new random password for every account you have created.
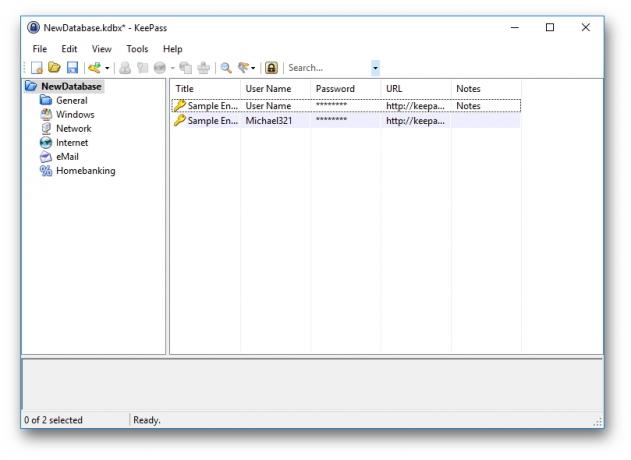
It is better to use a password manager, keeping its base locally. Excellent choice - KeePass. It has open source, has clients for all popular platforms and can protect your passwords with a passphrase and the key file. KeePass uses a strong encryption mechanism: even if a copy of your database is stolen, it will be absolutely useless to the attacker.
Download KeePass →
use Tor
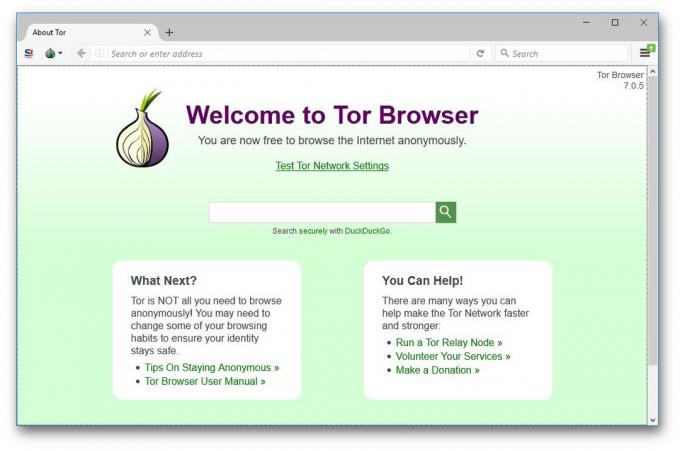
Even if you always use the incognito mode in Chrome or Firefox, we your actions on the web can still keep track of the Internet provider, the system administrator of your network or browser developer. To make surfing really private, it is necessary to use the Tor, which uses the principle of onion routing.
Download Tor →
If your ISP is blocking the download Tor, you can:
- Download from GitHub.
- Get an e-mail by sending the name of your operating system (windows, linux, osx) Address [email protected].
- Get through Twitter, sending @get_tor message with text help.
Of course, the speed of the network Tor leaves much to be desired, but not necessary to use it constantly. They can only be used to receive and transmit really important data. In other cases, use sites with the included secure connection by https. Preference is to give Firefox with telemetry was disabled.
Choose the search engines tested

You are tired, that Google and "Yandex" know everything that you are looking for on the Internet? go to alternative Search EnginesSuch DuckDuckGo. This search engine does not store information about you and ensures privacy.
DuckDuckGo →
Secure data storage in the cloud
To protect the information stored in the cloud, it is necessary to encrypt it. Even if the service is compromised, the attackers will not be able to read your data. This can be done using any utility for encrypting data, such as the built-in Windows BitLocker or VeraCrypt.
You can go ahead and create your own cloud with their home server. Use, for example, ownCloud. With it you can not only store files in their cloud, but also to raise their mail server and securely synchronize mail, calendar and contacts.
Download ownCloud →
Use an anonymous email service
Google's servers are browsing the contents of your e-mail messages to display targeted advertising. Other e-mail providers do the same. How to deal with it? Obviously, do not use Google Mail, "Yandex" and their ilk.
Instead, you can try:
- Protonmail. Anonymous email service to open source. Provides End-to-End encryption. This means that only you and your recipient can read the correspondence. It supports two-factor authentication.
protonmail →
- Tutanota. Another anonymous email service. The source code is open. Tutanota automatically encrypts all your messages and contacts on your device.
Tutanota →
- Your own mail server. Safe and encrypted as much as you want. Naturally, in order to raise your server, you need some knowledge. but all necessary information can be found on the Internet.
Go to the private messenger
Skype, Telegram, Viber, WhatsApp and other proprietary messengersCertainly convenient, but have a number of critical deficiencies related to privacy. What kind of privacy can say, if your correspondence is stored on a remote server?
To preserve the confidentiality of correspondence, use of decentralized messengers. They do not use servers, connecting users directly to customers. The most popular options:
- Tox. Advanced P2P messenger. Tox is completely decentralized, securely encrypted communication between users. There are clients for Windows, Linux, macOS and Android. Supports voice, video, screen demonstration, you can create a conference.
Download Tox →
- Ring. Capable of working as a centralized SIP-client, use your home server or act decentralized. There are clients for Windows, Linux, macOS and Android.
Download Ring →
- Retroshare. Creates an encrypted connection between anonymous clients, providing the opportunity to correspond, to carry audio and video calls, share files, and read the forums and subscribe to news channels. Works in Windows, macOS and Linux.
Upload Retroshare →
- Bitmessage. Another P2P messenger with open source. Decentralized protocol, message encryption and authentication using randomly generated keys make it very reliable. Only supports text conversation. There are clients for Windows, macOS and Linux.
Upload Bitmessage →
- Tor Messenger. Anonymous cross-platform messenger for advanced users using Tor. Encrypts correspondence. Do not use servers, communication goes directly between clients. Supports Windows, macOS and Linux.
Download Tor Messenger →
Install Linux
Consider switching to Linux. You can as much as necessary to disconnect the telemetry in Windows or MacOS, but you have no guarantee that it will not turn back with the next update. Operating systems with closed-source cause less confidence than Linux.
Yes, there is some specific applications on Linux. But for the Internet and entertainment it is well suited. If you still can not do without programs that are not on Linux, such as Adobe package, or you want to play games that are only available for Windows, you can install Microsoft's system to dual with Linux or in a virtual environment and to disable access to it Internet. Your data will not be corrupted by viruses or stolen, if the store them on an encrypted partition with Linux.
Popular Ubuntu is not the best choice because Canonical has recently been cooperating with Microsoft, in Ubuntu even suspected the existence of telemetry. For users concerned about privacy, you should use the supported distributions community: a simple and stable Debian or difficult to install, yet flexible Arch.
Forget about cell phones
If you're really paranoid, you have not used mobile phone. Instead, you can buy a USB-modem, plug it into the netbook and calls via VoIP with AES-encryption.
If you do not want to go so far, but still worried about the privacy of their phone calls, buy a smartphone on Android and install open source third-party firmware on it, eg LineageOS (Former CyanogenMod). Do not use the phone on Google services. Do not install the Google Play, use the third-party repositories such as open F-Droid. And install it on your phone Adblock.
Absolute privacy is unattainable in principle. But the listed techniques can protect you from identity theft scams, from curiosity colleagues sitting with you at the same table, the annoying attention of marketers and Google Microsoft.



